Get insight into your laptop’s status and taking some precautions with CPUID’s Hardware Monitor and CPU-Z and Belarc Advisor It happens to most laptops eventually. After two or more years of heavy (ab)use, most of our laptops are not in the condition they were...
SPK Blog Post
3-Step Fix for your rr.nu WordPress Virus Outbreak
Symptoms of the rr.nu Wordpress Virus: Wordpress-based websites infected with the virus are redirecting visitors to a fake virus-scan website. The URL looks like http://*.rr.nu. When you check the files on your server, the following line is inserted into your .php...
Test Management 101 – Why Developers Are Not Sufficient to Fully Test Your Project
Your developers have been working on your latest software project. The hours have been long, the going a little rough, and they're just about finished in more ways than one. Now it's time to verify that the application works. Are you thinking of asking your developers...
Five Steps to Take if Your IT Outsourcing Agreement Goes South
IT outsourcing relationships can be fraught with challenges, ranging from communications breakdowns between client and provider to issues surrounding performance. If an IT outsourcing agreement isn’t meeting your company’s expectations (e.g. SLA targets are missed;...
Distinguishing Between Virtual Teams and IT Outsourcing
One of the benefits of an IT outsourcing partnership is that it can offer companies the option of working with virtual teams who can help support different types of IT and business operations, regardless of the locations of the workers. Teams and team members who work...
How to Setup License Statistics Free Version
Software asset management tools, particularly license usage and monitoring software are gaining more and more interest among large corporations. It should come as no surprise since by utilizing such tools they stand to gain upwards to 10% in cost reductions and that...
Software Development Using Kanban
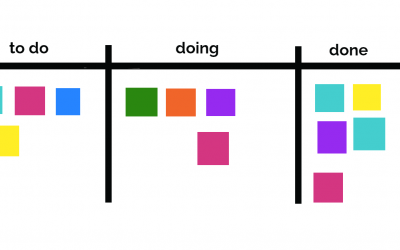
Software Development Using Kanban The SPK development team engages with customers utilizing agile principals. This typically means incremental sprint deliveries of code as part of a scrum model. At a recent engagement, we employed an interesting variation of this...
Security basics with IPTables
When on the internet, there's always concerns of security. If you're listening on some services but not others, you need to modify the Linux firewall to allow this. Also, if there's undesirable clients accessing ports and hacking, IPTables is an effective...
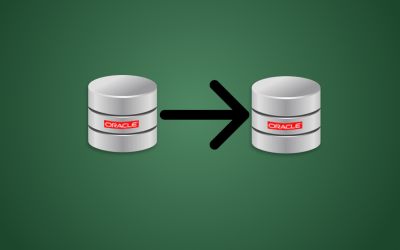
Oracle Database Cloning Made Easy
As a systems integrator, I spend my time behind a variety of applications every day. Each of these applications stores its data in some type of database. The most common databases I deal with are typically MySQL, Oracle, DB2, Postgres, and MS SQL Server. As such,...
Bad Changeset Management, Release Management Can Be Disastrous for Your Company
The core activities of configuration management (i.e. changeset management and release management) are essential to control the changes made to a system and to administer the release of its different versions. However getting it wrong damages your brand, customer...
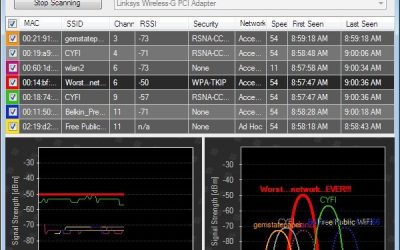
Using inSSIDer to be a good wireless neighbor
Have you ever noticed that the wireless neighborhood is seemingly always located in the bad part of town? This is especially true in the crowded wasteland of the 2400 block of Megahertz Ave. Where might you find this undesirable neighborhood? Unfortunately, the answer...
Integrating Meld with Git under Linux
Have you ever used Git? Git has quickly grown to become one of today's most popular source code management solutions for software engineering projects large, small, professional and personal. Developed by Linus Torvalds, Git is classified as a “distributed version...