Ensuring product security is a top priority for manufacturing companies. Although there are constant risks to security, they are avoidable. Threat modeling can help reduce, lessen, or fully prevent these risks. Let’s explore how threat modeling ensures the best security.
What is Threat Modeling?
Before we dive into the benefits of threat modeling, let’s define it. Threat modeling is a set of actions applied to a system or product to enhance security. These actions are designed to detect potential risks and develop both preventative and remedial defenses against them. There are five main steps in this process.
Steps of Threat Modeling
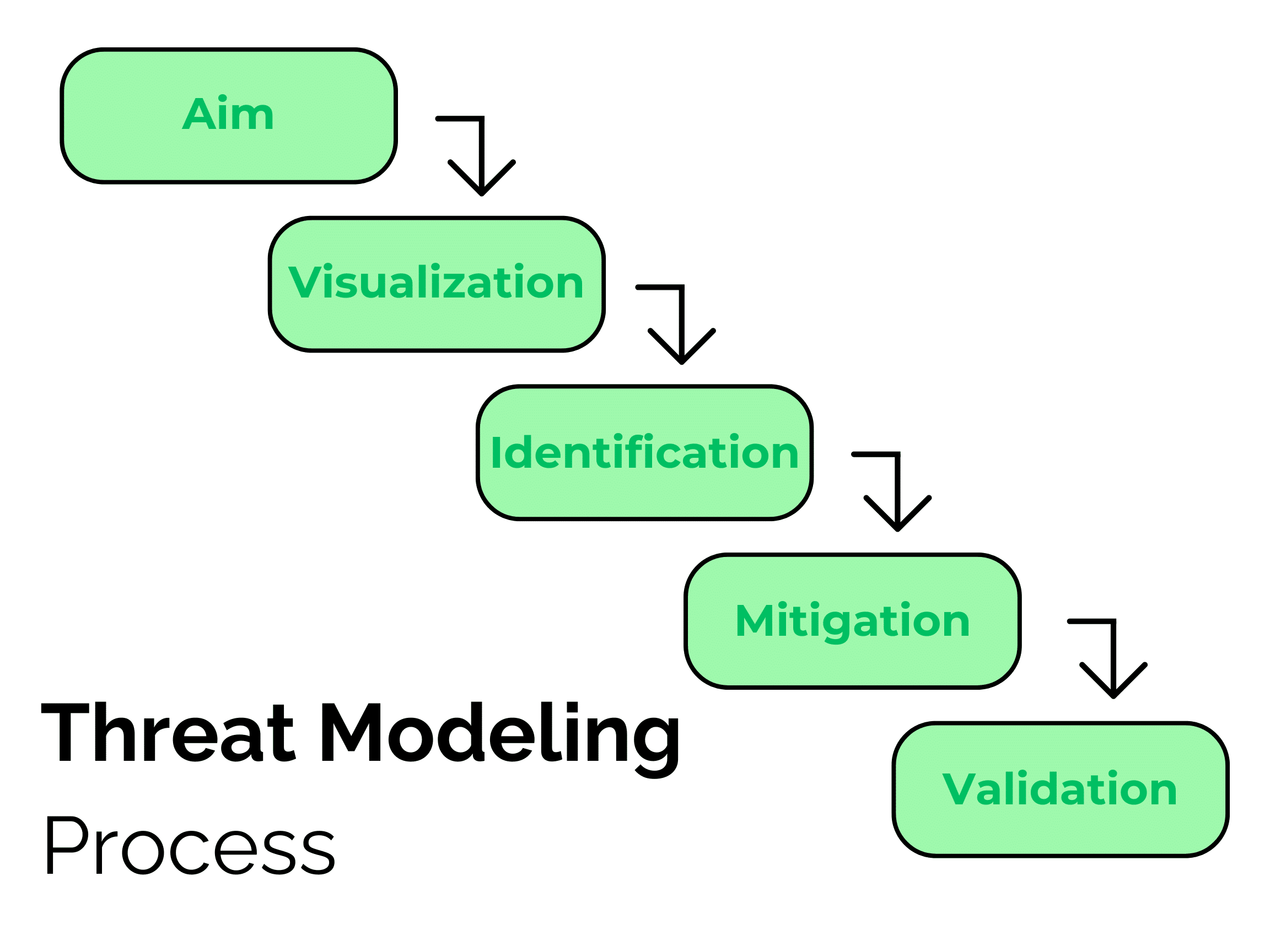
- Aim – The first step of threat modeling is to define the scope of the product or system. Set parameters for what you aim to achieve. The goal of this step is to identify weaknesses and create an understanding of how the following steps should be implemented.
- Visualization – Next, gather data and decide which assets are the most important to protect. This will most likely include significant data and intellectual property.
- Identification – After deciding the most important items to protect, identify potential threats that may compromise the system. These threats may be anything from a system failure to a hacker.
- Mitigation – The threats identified are now ready to be mitigated. Put your security practices in place to prevent and eliminate future attacks. This step includes updating security controls to ensure threats cannot bypass security measures.
- Validation – The last step is to verify and validate the elimination of threats through documentation. Documenting the process adds an extra layer of security, decreasing the chances of a threat bypassing the preventative measures.
These steps can be applied across industries, but we will cover the two main types of cybersecurity threat modeling benefits. These are R&D and endpoint security.
R&D vs Endpoint Cybersecurity
Research and Development (R&D) cybersecurity aims to protect sensitive information within research departments. It entails safeguarding specialized software, research databases, and collaboration tools. For example, R&D handles system failures that risk intellectual property loss. Along with this protection, it helps ensure compliance and reduces internal and external threats, which we covered in this blog.
Endpoint security on the other hand protects the devices used to connect to a network. This includes computers, tablets, phones, and IoT devices. The main form of endpoint security is cyber attack prevention. Devices that connect to a computer network, otherwise known as endpoints, are frequently targeted by malicious actors. If the attacker succeeds, malware could be installed or data could be breached.
Benefits of Threat Modeling
R&D Cybersecurity
In all instances, threat modeling aids in keeping data safe. For R&D, threat modeling first identifies how data flows through the environment. Understanding data flow illuminates the points that need the most protection. After this, threat modeling assesses all individuals who have or want access to critical information. These individuals pose security threats. They may be anyone from contractors to competitors. In addition to this, threat modeling assesses access controls, ensuring there are no gaps unauthorized users could bypass. To expand on this, threat modeling also encourages developing practice scenarios, allowing users to understand what an attack looks like. For example, a user can simulate a malware infection. Lastly, based on their findings, users implement security controls such as encryption and advanced monitoring to keep data safe.


Endpoint Cybersecurity
Threat modeling for endpoint security has some differences, but the same goal as R&D. The first way threat modeling helps ensure security is by organizing devices and data. Identifying what devices and data are available to hackers is a start. After this, the threats are identified. For endpoints, these are typically phishing and malware attacks. In addition to threats, software vulnerabilities and configuration weaknesses are identified. Common vulnerabilities in endpoints include outdated software and unpatched systems. Knowing these vulnerabilities, users can develop a high-risk scenario. For example, users may navigate what to do when an endpoint is compromised due to insecure Wi-Fi. Once they understand the risks, users can implement preventive measures. Endpoint measures include anti-malware, antivirus, and EDR solutions. Lastly, threat modeling encourages strict access controls and enforces strong authentication methods.
Putting Threat Modeling in Action
As displayed through these examples, threat modeling has many benefits for eliminating risks for new products. It provides a step-by-step approach to ensure data protection. By helping organizations understand threats and prepare for attacks, threat modeling gives organizations confidence in their security efforts. If you have any questions or want to help secure your next product going to market, contact one of our experts today.








