In recent years, remote work has become the norm for many organizations. With workers all around the globe on different networks, cybersecurity risks are much higher. System failures and hackers still pose risks even when working on the same network. All of these threats are causing organizations to assess their security level. A great way to increase security, especially for companies who implement CI/CD pipelines is administering zero trust architecture.
What is Zero Trust Architecture?
Zero Trust Architecture (ZTA) is a strict framework that enforces the verification of every aspect that comes into contact with a network. It is called zero trust as it is trained to not trust anything or anyone until it verifies it is not a cybersecurity threat. This security model is drastically different from the typical model, which assumes internal aspects can always be trusted. Threats can be both external and internal, which is why ZTA is necessary. ZTA considers all data sources and computing services resources that must be protected.
Some main components of Zero Trust Architecture are explicit verification, limited access, and breach assumption. These features ensure all data points are authorized, users are not accessing unnecessary areas for their roles, and networks are continuously monitored to prevent breaches. Two common practices in ZTA architecture for verification are Identity and Access Management (IAM) and Multi-Factor Authentication (MFA). When it comes to access, the least privilege principle is often employed. This principle ensures users only access the parts of the network required to perform their tasks.
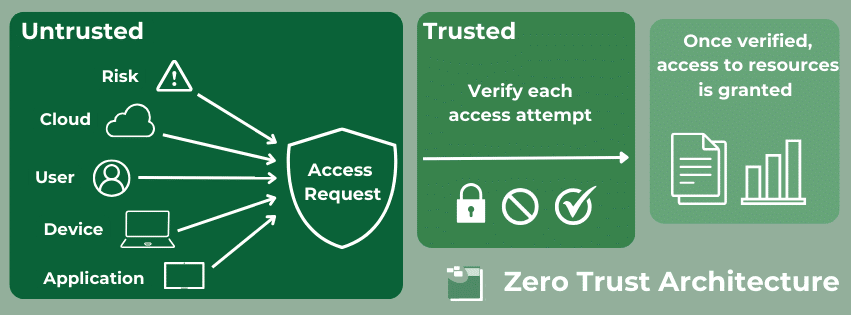
Additional security measures include device trust and continuous monitoring which evaluate the devices and users accessing the network. Furthermore, ZTA encourages all data to be encrypted and all communication to be secured. Even if an individual works from the company’s office on their network, it does not mean their conversations are immune to security risks. The last common ZTA practice we will cover is microsegmentation. This is when an organization divides its network into small segments to individually secure each, rather than trying to secure one large network.
What Are CI/CD Pipelines?
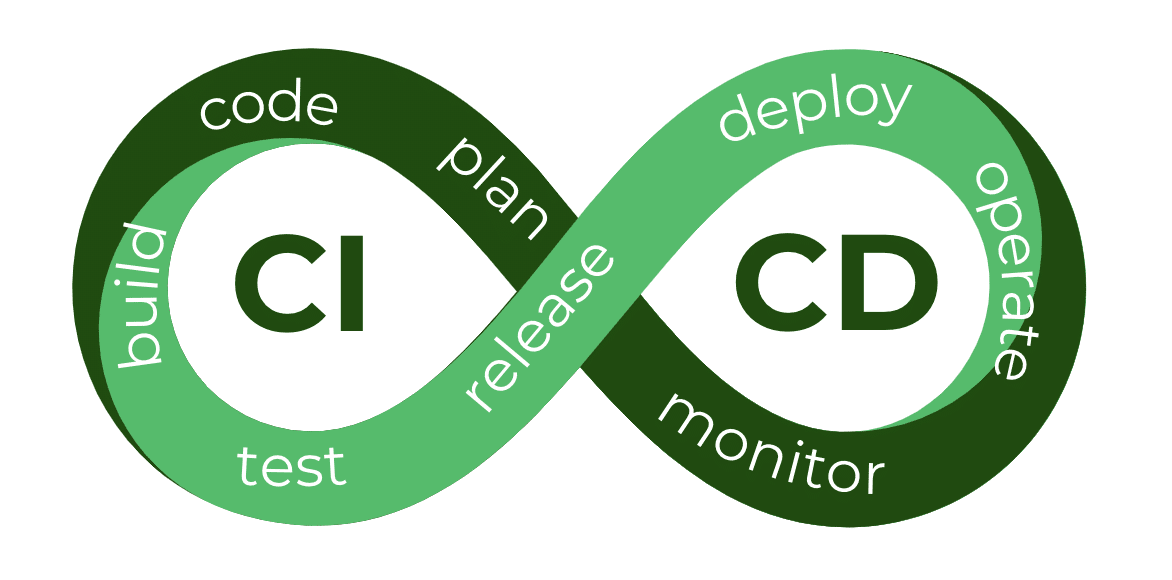
Zero trust architecture can be applied in multiple contexts, but today we are exploring the benefits specific to CI/CD pipelines. Continuous Integration and Continuous Deployment (CI/CD) are software development methods used in coding. Continuous Integration involves consistently merging code changes into a central repository. This helps identify integration issues early in the process. Each integration is verified by automated tests which ensure the software can keep deploying. Developers are notified of all integrations so they can quickly address issues if or when they occur. The goal of CI is to reduce delivery times and enhance software quality.
Continuous Deployment is the practice of allowing code changes to make their way through the entire software development pipeline. Its goal is to automate software releases, ensuring faster time to market. The continuous deployment of code changes ensures improvements such as bug fixes or new features are efficiently delivered without the need for a developer. This process entails sending code changes through automated test and deployment stages. In addition to this automatic deployment, CD ensures a fast feedback loop that quickly delivers improvements.
There are a few main components of CI/CD pipelines. The first one which we briefly mentioned earlier is automated testing frameworks. These frameworks are used to verify code changes. Additionally, CI/CD pipelines have a Version Control System (VCS) which is used to manage and track code changes and integration. Other important features include tools for code-building, deployment automation, and monitoring.
How to Implement ZTA for CI/CD Pipelines
When implementing Zero Trust Architecture there are a few easy steps to follow:
- Identify Assets: Understand and classify assets such as deployment environments, code repositories, and integrations.
- Authentication: Ensure access to CI/CD pipeline is secure with MFA and IAM.
- Microsegmentation: Divide the network into segments and enforce strict access controls for each.
- Automation: Utilize CI/CD’s automated pipeline to enforce security practices.
- Encryption: Ensure data is encrypted throughout the entire pipeline.
- Monitoring: Continuously monitor and log any issues with the data.
In addition to these steps, there are other ways to make CI/CD pipelines more secure. According to Sharon Goldberg, a speaker at DevOps Day Raleigh, one way to ensure safe pipelines is by minimizing the reuse of long-lived secrets. Sensitive information can be hard to rotate if it’s in multiple places throughout the pipeline. This can serve as a security risk. Sharon also emphasizes the importance of other zero-trust practices such as limited access and logging.
Benefits of ZTA for CI/CD Pipelines
The obvious reason for implementing Zero Trust Architecture is to ensure security, but there are additional benefits for CI/CD pipelines. First, let’s cover the security benefits. Some practices like microsegmentation and the least privilege principle severely lessen the risk of internal and lateral attacks. Others such as controlled third-party access ensure all integrations are monitored, reducing threats to the supply chain. Lastly, access controls and data encryption protect sensitive data from unauthorized access. While managing this can be a bit more overhead, the benefits definitely outweigh the additional work, especially when you look at the impact of a widespread exploit.

ZTA offers more than these security benefits. For example, ZTA supports scalability without compromising any of the amazing features of CI/CD pipelines. Additionally, it offers increased resilience with threat detection and rapid incident response times. Furthermore, ZTA enhances efficiency in the automation process. It verifies code, securely deploying only trusted pieces. Lastly, it improves compliance for pipelines. Not only does it ensure the application of consistent security policies within industry standards, but it also automates regular compliance checks.
Ready to Implement ZTA for CI/CD Pipelines?
Zero Trust Architecture has many benefits for CI/CD pipelines including enhanced security, compliance, and scalability. Although ZTA can have complexities with deployment and management, it is worth the effort. With ZTA, organizations can worry less about internal and external threats. If you have questions or want to implement ZTA for your business, SPK’s experts can help. Contact us today.






