Overview In 2015, SPK and Associates co-founder Chris McHale spoke with Peter Thorne, Director at Cambashi, a Cambridge, England-based independent industry analyst firm. With his over 30 years of experience as a software engineer user, vendor, and now analyst, Peter’s...
Compliance & Regulatory
Version Control in CAD: Why It’s Critical for Compliance and Collaboration
Hi everyone, I am Daniela, and I am the CAD SME for SPK and Associates. Today we'll be discussing version control in CAD. Why Version Control in CAD Matters Version control in CAD is mission-critical for maintaining your CAD resources. It really ensures stability,...
Enhancing Traceability and Compliance with PTC Windchill
As complex, smart, and connected products become the norm, manufacturers must contend with increasingly stringent regulations. Traceability and compliance are mission-critical. Manufacturers must also meet rising customer expectations and overcome unpredictable supply...
Streamlining Document Organization and Compliance with Document Vault in Jira Cloud
Protecting documentation inside project tools like Jira Cloud can be a challenge in regulated environments. Whether you're managing technical files, contracts, or quality compliance records, attachments are often scattered and exposed to unnecessary users....
How Medical Device Engineers Can Streamline CAD Workflows for Faster FDA Approval
Balancing speed and compliance in medical device engineering can be challenging. Engineers face tight deadlines and detailed requirements to bring life-saving products to market. Your CAD workflows should aid in the path to compliance and accelerate FDA approval. As...
EU Digital Operational Resilience Act Compliance 101: What Financial Institutions and ICT Providers Need to Know
Digital disruptions such as cyberattacks or system failures are one of the largest threats to the financial sector. Recognizing the increasing reliance on digital infrastructure, the European Union introduced the Digital Operational Resilience Act (DORA). This act...
Achieving Zero-Downtime Nightly Releases in a Highly Regulated Environment
Market traders understand the importance of timing in the trading industry. Each day missed (or hour missed) is considered lost revenue. When a proprietary trading firm began to miss trading days due to issues with its software, leaders of the firm contacted SPK to...
How SPK’s Application Management Services Solved Klocwork License Tracking Challenges
Effectively managing software licenses can be challenging, but it is critical in ensuring your organization works cost-efficiently. These challenges only increase when vendors make unexpected changes. This was precisely the case when Klocwork, a leading static code...
Accelerating Medical Software Compliance and Efficiency with SPK ACEs
Compliance with regulatory standards is the number one priority for every medical manufacturer. Ensuring pipelines are secure and compliant doesn’t just ensure safety, but it results in better quality products. When a startup medical manufacturing company contacted...
The FDA UDI Rule: 5 Things You Need to Know
The release of the FDA final rule on Unique Device Identification (UDI) is expected this summer. Here are five things you need to know: 1. What is the UDI Rule? In July 2012, the FDA proposed a rule requiring medical device manufacturers to label their products with...
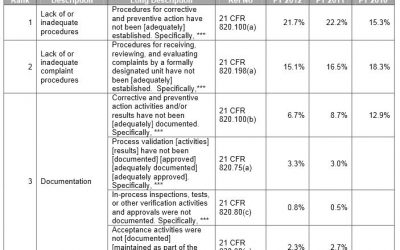
FDA Form 483: Top Ten Observations for Medical Devices
Medical Device manufacturers regulated by the FDA are subject to cGMP (Current Good Manufacturing Practice) regulations and may be inspected by the FDA to ensure compliance. If the FDA inspector(s) observes conditions that in their judgment may constitute violations,...
7 Steps for Implementing ISO 9001 Quality Systems Successfully
Implementing a Quality Management System (QMS) that ensures compliance with ISO 9001 is a strategic decision for organizations. Implementing this system enhances customer satisfaction, improves efficiency, and drives continuous improvement. However, achieving ISO 9001...