Any project can be divided into different parts including requirements gathering, design, implementation, documentation and so on. One key aspect of the project lifecycle is quality assurance (QA), but it's often overlooked. Although almost all project managers...
Engineering Operations
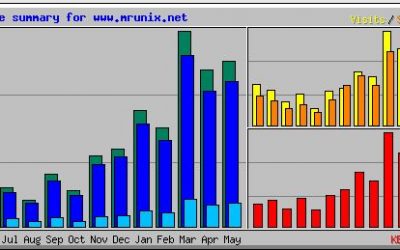
Setting up Web metrics with Webalizer
When managing websites, it's important to have metrics on the site for both admin and content owners. One of the easiest ways to do this is Webalizer. It is a free tool that uses the Apache access log to provide a graphical presentation of usage. Attached is a quick...
How to add more disk space to your Redhat server without reformatting
One of the common tasks for any system administrator is managing disk space on a server. It doesn't matter what operating system the server is running, free disk space is always something you keep an eye on. I won't go into a boring lecture on why managing disk space...
Outsource Your System Administration to Set Your Engineers Free
The inquisitive nature of engineers, which makes them so good at designing, developing and building products, can also lead them to become distracted by other “interesting things” like managing the very systems and tools that allow them to do their engineering....
In Celebration of IPv6
On June 8th of last year, an event known as World IPv6 Day was celebrated. Well, “celebrated” might carry a little too much emphasis – perhaps instead, World IPv6 Day was observed. And what did you do to celebrate this observance of the future? Well, if you are like...
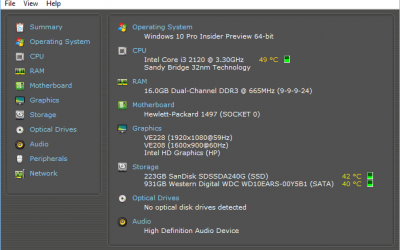
Using Speccy to Understand What’s Inside Your Computer
This week we’d like to cover a tool that assists with understanding what is actually in that desktop or laptop you work with. Most of us know in lesser or greater detail that there is a CPU, some random access memory (RAM) a hard disk drive (HDD), various peripherals...
How to Obtain Electric Commander Metrics for Use in a GWT Plugin
Developed by Electric Cloud, Electric Commander is an extremely versatile tool for enhancing and automating your organization’s software development build-test-deploy cycle. Commander makes it possible to eliminate unnecessary lag time between phases of the...
Get Insight Into Your Misbehaving Laptop With Three Free Tools
Get insight into your laptop’s status and taking some precautions with CPUID’s Hardware Monitor and CPU-Z and Belarc Advisor It happens to most laptops eventually. After two or more years of heavy (ab)use, most of our laptops are not in the condition they were...
3-Step Fix for your rr.nu WordPress Virus Outbreak
Symptoms of the rr.nu Wordpress Virus: Wordpress-based websites infected with the virus are redirecting visitors to a fake virus-scan website. The URL looks like http://*.rr.nu. When you check the files on your server, the following line is inserted into your .php...
How to Setup License Statistics Free Version
Software asset management tools, particularly license usage and monitoring software are gaining more and more interest among large corporations. It should come as no surprise since by utilizing such tools they stand to gain upwards to 10% in cost reductions and that...
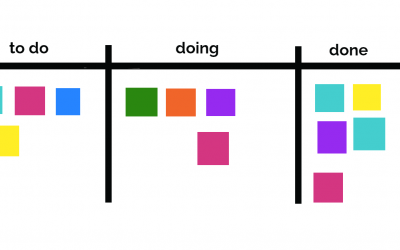
Software Development Using Kanban
Software Development Using Kanban The SPK development team engages with customers utilizing agile principals. This typically means incremental sprint deliveries of code as part of a scrum model. At a recent engagement, we employed an interesting variation of this...
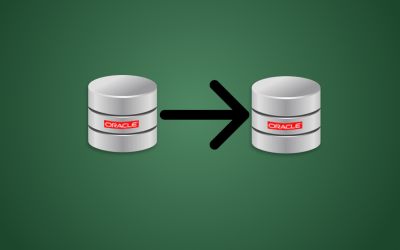
Oracle Database Cloning Made Easy
As a systems integrator, I spend my time behind a variety of applications every day. Each of these applications stores its data in some type of database. The most common databases I deal with are typically MySQL, Oracle, DB2, Postgres, and MS SQL Server. As such,...