Repeatability is a intuitive aspect of daily life. If you throw a ball up, it must come down. If you throw it twenty times, the same thing will happen, up and then down. When repeatability doesn't occur we get anxious. Repeatability is equally an essential quality in...
Infrastructure
Outsourcing is the Best Way to Stay Flexible, Even Elastic!
The technology industry loves buzzwords. The decade of the '80s was all about synergy and paradigm shifts. In the '90s, it was the web and the Internet. The turn of the century brought talk about virtualization and social media. Today it's all about the cloud. Of...
Macs in a Corporate IT Environment
Macs running OS X have been around for quite some time, but only recently have they gained enough traction with our customers at SPK to be used as their day to day desktop environment. Historically, IT organizations have been reluctant to embrace this change. This...
To SSD or not to SSD
What is an SSD? The term SSD (Solid State Drive), can refer to any drive that uses solid state components to store information, or more to the point - has no moving parts. When we hear terms like 'Flash Drive' or 'Thumb Drive', we typically don't think SSD, but...
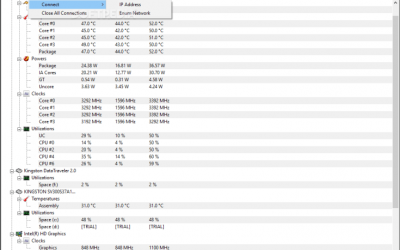
Upgrade to HWMonitor Pro and Make Your Computer’s Sensors Work For You!
Some time ago, I wrote an article about CPUID’s wonderful tool, HWMonitor. Today I want to follow up on that and give a few tips on how to make it more useful. Firstly, HWMonitor is a free tool, but CPUID publishes a Professional version of the product, predictably...
5 Minutes with Windows 8 and Office 2013
Dell Latitude ST This is the Dell Latitude ST, which can be had from the Dell Outlet store for about $300. It’s a 10-inch tablet slate running an Atom Z670 and 2GB of RAM – like a Netbook without a keyboard. Instead, it has an N-trig digitizer that supports both...
How to Install Snort on a Redhat 6 Box
Snort is used for performing security checks on network boundaries. This can be done on the outside Untrust network but is sometimes more useful to look at what’s getting through your firewall into the web servers. Follow our step-by-step instructions on how...
How to Create a Silent Installer for ANSYS 14
I'm a huge fan of automation, especially when it comes to installing software. With a simple one-click solution, you can setup software on a user's workstation with little or no impact on your work load. In fact, you don't even need to do the installation -- users can...
Do you Think an Engineering Employee is Really Cheaper Than a Consultant? … Think Again.
Occasionally I’ll get a comment from a potential client who is particularly price sensitive about the rates for our consultants, and the comment usually goes something like: “I can hire a full-time employee who would cost me a lot less than what you are going to...
Deploying IPv6 on a Cisco IOS router with a Tunnel Broker
The time has finally come! Just a few days ago, major internet companies participated in IPv6 Launch Day – meaning from this point forward, they will be running their production systems and making their services available to you via the IPv6 in addition to IPv4....
Gain Greater Control Over Windows Disk Defragmentation with Defraggler
This week we have a look at an alternative to Windows Disk Defragmenter. Piriform has a number of Windows utility offerings, among which is Defraggler. Defraggler has the following capabilities, a number of which are not available with the Windows default utility. 1....
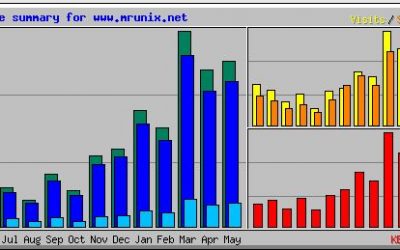
Setting up Web metrics with Webalizer
When managing websites, it's important to have metrics on the site for both admin and content owners. One of the easiest ways to do this is Webalizer. It is a free tool that uses the Apache access log to provide a graphical presentation of usage. Attached is a quick...