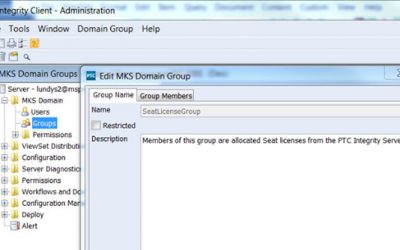
When it comes to licensing your PTC Integrity Lifecycle Manager server, you have the option of either purchasing seated licenses, floating licenses, or some combination thereof to service your user community. In this blog, I am going to discuss how to implement seat...
Software Development & Release Management
Three Monotonous Tasks That Are Killing Morale In Your Software Engineering Team
In the engineering world, there’s no underestimating how hard it is to attract and retain top talent. Finding qualified candidates is hard enough. But you want to go one better than that. You want to attract talent that gives your organization a competitive edge. Once...
Electric Flow 8.0 New Feature: Manual and Automated Retry on Error
Electric Cloud recently released version 8.0 of their build and deployment orchestration tool, Electric Flow. This latest release includes many new features, but the focus of this article will be the ability to retry tasks and stages from a failed pipeline and why...
Podcast: Can IoT Jump These Five Hurdles? Episode 2 – Sensor Interfaces and Smart Devices
In the second episode of our podcast series "Can IoT Jump These Five Hurdles?", we transition from a broad introduction of these five hurdles to a deeper dive into each challenge facing the Internet of Things. Let's begin with the smart device itself and it's digital...
Creating and Deploying a Docker Image
Sed convallis purus a leo cursus, blandit laoreet diam viverra. Aenean quis lacinia risus. Etiam mollis, lectus efficitur luctus consectetur, enim magna lobortis est, et congue turpis lorem in nisl. Nulla urna metus, rhoncus nec vulputate eu viverra fusce.
SPK Develops Dashboard for E*Trade’s Electric Commander
Why are dashboards important? In a nutshell, they allow you to visually present information in a way that is meaningful to the reader. They allow the reader to immediately see trends, and more importantly, quickly make decisions or change behavior in order get better...
Continuous Integration Best Practices—Part 4
As I noted in other articles in this "Continuous Integration Best Practices" Series (click here for Part 1, Part 2, or Part 3", there are 10 best practice principles associated with Continuous Integration and in this previous articles, we covered the first eight. In...
Continuous Integration Best Practices—Part 3
As I noted in "Continuous Integration Best Practices—Part 1" and "Continuous Integration Best Practices—Part 2" there are 10 best practice principles associated with Continuous Integration and in this previous articles, we covered the first six. In this article, we...
Today’s Growing IoT Problem: Embedded Software Security – An Interview with Cambashi’s Peter Thorne
When it comes to the Internet of Things (IoT) and connectivity, embedded software security is a top concern for a growing number of manufacturing companies and their software engineers. The worldwide market for embedded security software is forecasted to rise to $2.95...
Continuous Integration Best Practices—Part 2
As I noted in "Continuous Integration Best Practices—Part 1" there are 10 best practice principles associated with Continuous Integration and in this previous article, we looked at the first three. For part 2, we pick up where we left off and talk about principles...
Continuous Integration Best Practices—Part 1
Continuous Integration is a leading software development methodology whereby new development is constantly being submitted and tested against the main body of work. The goal being rapid feedback on incremental changes, resulting in lower maintenance costs and higher...
The Difference Between Continuous Integration and Continuous Delivery
If you've spent any significant amount of time in the world of DevOps and Agile software development practices, you've likely encountered the terms Continuous Integration (CI) and Continuous Delivery (CD). For several years, I've had these terms thrown around me...